Private networks have gained significant attention in recent years as organizations seek to leverage the benefits of 5G technology for their specific needs. These networks offer enhanced security, lower latency, and increased reliability compared to traditional public networks. When deploying a private 5G network, enterprises have several deployment options to choose from, each with its own advantages and considerations.
In this article, we will explore three common deployment models for private 5G network.
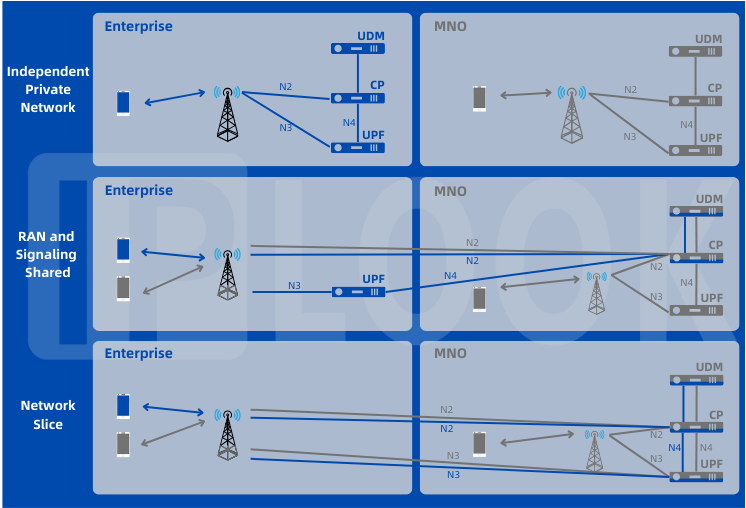
The independent private network model involves an enterprise deploying and operating its own standalone 5G network infrastructure. This model provides the highest level of control and customization for the organization. It typically includes setting up a dedicated RAN, core network, and associated infrastructure. By building their own network, enterprises can tailor it to meet their specific requirements, ensuring optimal performance and security. This model is particularly suitable for organizations with unique needs or stringent security and performance requirements.
In the RAN and Signaling Shared model, the enterprise handles local services while sharing the RAN, including spectrum, with the public network. In this scenario, the MNO maintains control over network and user management. The N2 interface, which connects the RAN to the core network, is terminated at the 5GC within the public network domain. This model allows the enterprise to benefit from the MNO's existing network infrastructure and expertise while maintaining control over localized services. It is a suitable option for organizations that require localized control and customization but also want to leverage the MNO's infrastructure and resources.
Network slicing is a fundamental feature of 5G technology that enables the creation of multiple virtual networks within a shared physical infrastructure. In the Network Slicing model, 5G networks are divided into logical slices, each tailored to specific applications or user groups. Each slice has its own dedicated resources, network architecture, and Quality of Service (QoS) parameters. This model ensures logical separation and resource isolation, allowing organizations to protect the Service Level Agreements (SLAs) of each enterprise or application. By leveraging network slicing, organizations can create separate virtual networks with customized characteristics while sharing the underlying infrastructure.
It is important to note that the aforementioned deployment models are representative but not exhaustive. Different enterprises in different industries may choose combinations or variations of these models based on their specific requirements and circumstances. For example, an organization may opt for an independent private network for its critical operations while utilizing network slicing for certain applications within that network.

